Recently Completed The Engineering Virtual Program by Goldman Sachs.
The main topic of this program was to crack passwords from the leaked database containing the hashes.
Topics that I learned from this program--
(Note - An introductory level of knowledge about these topics was required for this program)
- Cryptographic hash function (CHF)
- Types and properties of different types of CHF
- Salt (cryptography)
- Password cracking tools and techniques
Cryptographic hash function(CHF)
A cryptographic hash function (CHF) is a mathematical algorithm that maps data of arbitrary size (often called the "message") to a bit array of a fixed size (the "hash value", "hash", or "message digest").
It is a one-way function, that is, a function for which it is practically infeasible to invert or reverse the computation.
A cryptographic hash function must be deterministic, meaning that the same message always results in the same hash. Ideally, it should also have the following properties:
it is quick to compute the hash value for any given message
it is infeasible to generate a message that yields a given hash value (i.e. to reverse the process that generated the given hash value)
it is infeasible to find two different messages with the same hash value
Types and properties of different types of CHF
- MD5
MD stands for Message Digest. MD5 was designed to convert plaintext into hashes, also known as "message digests," quickly and with a minimal amount of computation. That works in the favor of crackers. Armed with a single graphics processor, they can cycle through more than eight billion password combinations each second when attacking "fast" hashes.
- SHA
SHA-2 (Secure Hash Algorithm 2) is a set of cryptographic hash functions designed by the United States National Security Agency (NSA), first published in 2001.
The SHA512crypt function is included by default in Mac OS X and most Unix-based operating systems passes text through 5,000 hashing iterations. This hurdle would limit the same one-GPU cracking system to slightly less than 2,000 guesses per second.
- Salt (cryptography)
In cryptography, a salt is random data that is used as an additional input to a one-way function that hashes data, a password, or a passphrase. Salts are used to safeguard passwords in storage. Historically, only a cryptographic hash function of the password was stored on a system, but over time, additional safeguards were developed to protect against duplicate or common passwords being identifiable (as their hashes are identical). Salting is one such protection.
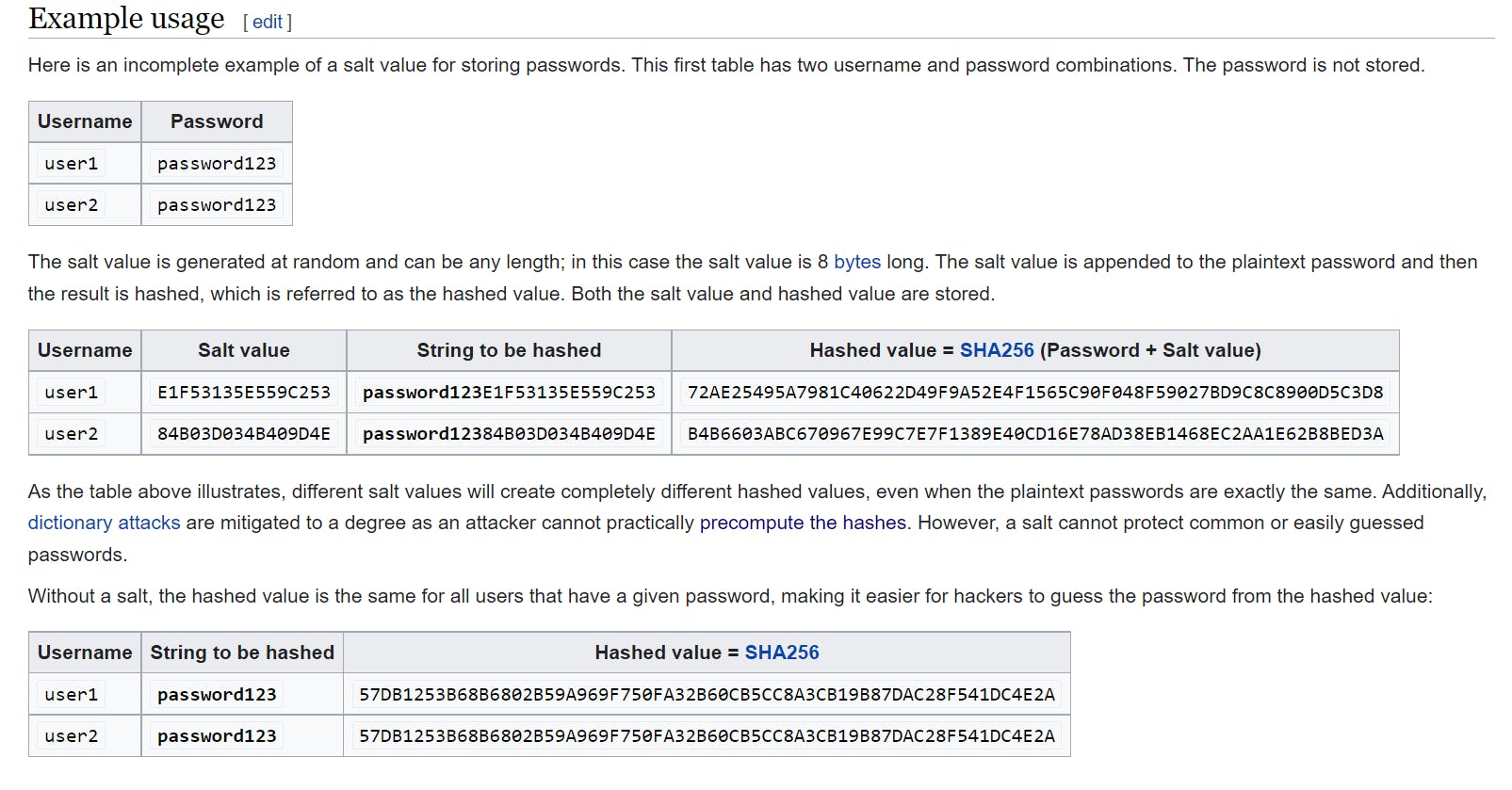
- Password cracking tools and techniques
One example is brute-force cracking, in which a computer tries every possible key or password until it succeeds. With multiple processors, this time can be optimized through searching from the last possible group of symbols and the beginning at the same time, with other processors being placed to search through a designated selection of possible passwords. More common methods of password cracking, such as dictionary attacks, pattern checking, word list substitution, etc. attempt to reduce the number of trials required and will usually be attempted before brute force. Higher password bit strength exponentially increases the number of candidate passwords that must be checked, on average, to recover the password and reduces the likelihood that the password will be found in any cracking dictionary.
There are many password-cracking software tools, but the most popular are Aircrack-ng, Cain & Abel, John the Ripper, Hashcat, Hydra, DaveGrohl, and ElcomSoft.
We would be using Hashcat in this case
Procedure
- Install Hashcat on Kali Linux or any Linux distribution
sudo apt-get install hashcat
Check for the documentation of Hashcat
hashcat -h-mis for Hash type0is for MD5-ais for Attack mode0is for StraightNavigate to Wordlist Folder
cd usr/share/wordlists
Here you would find the
rockyou.txtfilerockyou.txt contains 14,341,564 unique passwords, used in 32,603,388 accounts.
Kali Linux provides this dictionary file as part of its standard installation.
Perform the attacks on the given Hashes, and store the output in another text file.
-oDefines outfile for recovered Hash
For, Detailed Report, checkout my LinkedIn.

